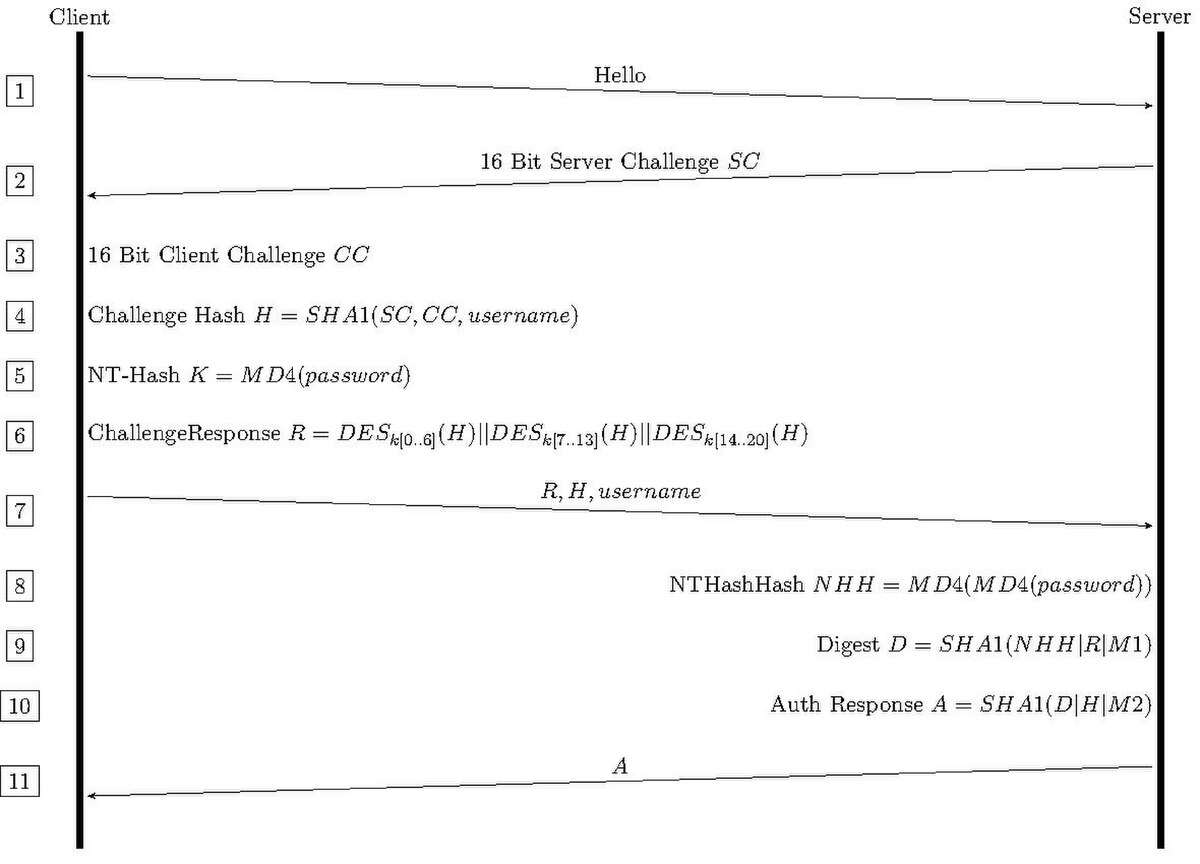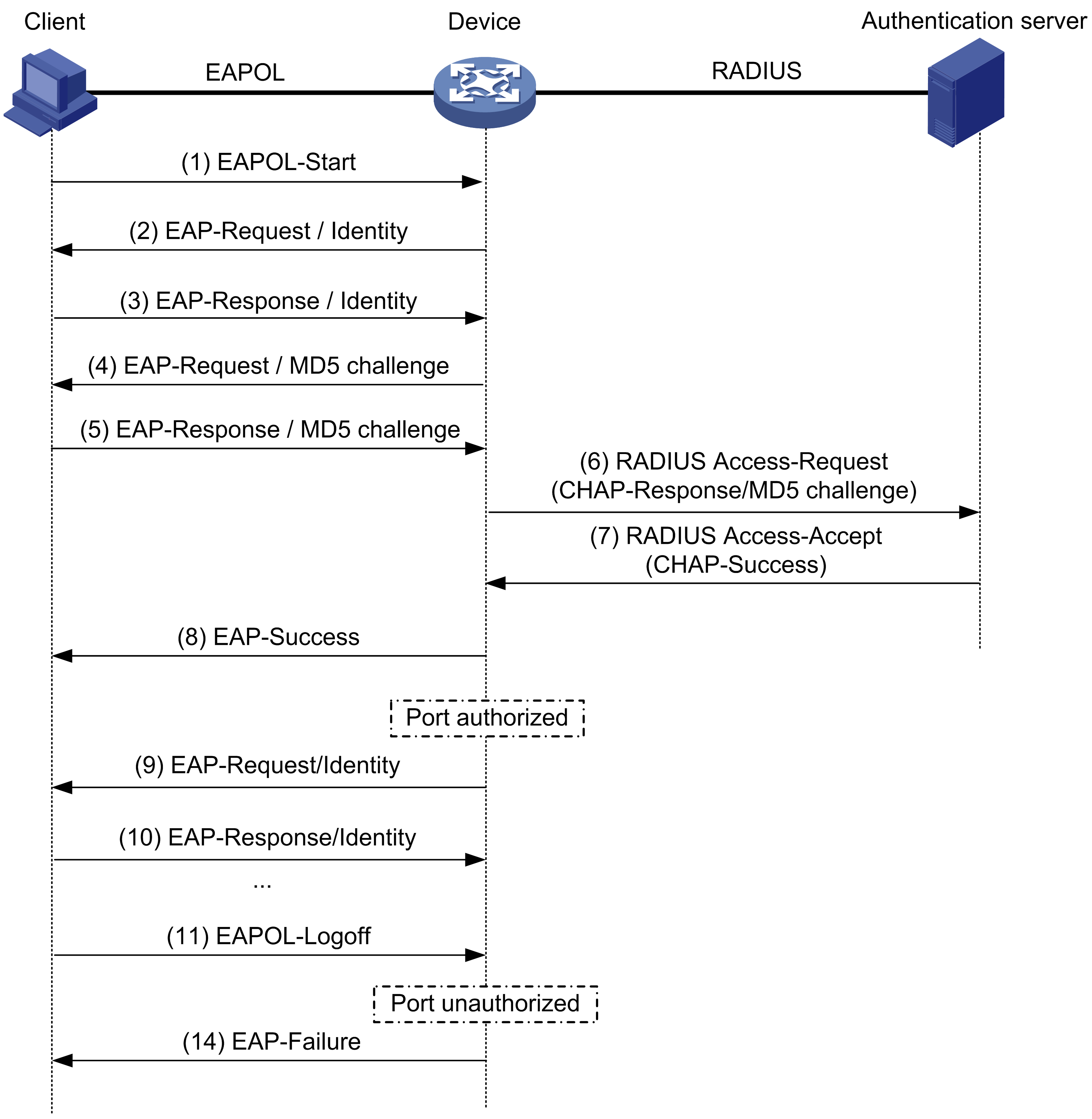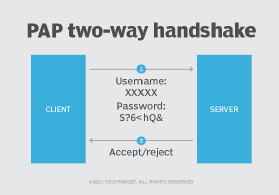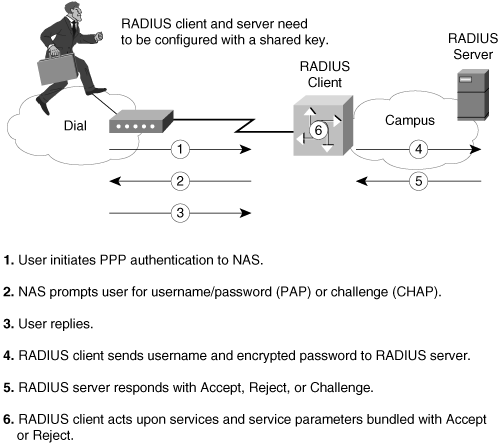
Authentication and Identity Protocols :: Chapter 2. Basic Security Mechanics and Mechanisms :: Wireless lan security :: Networking :: eTutorials.org
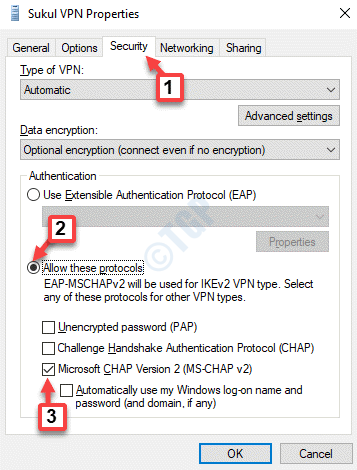
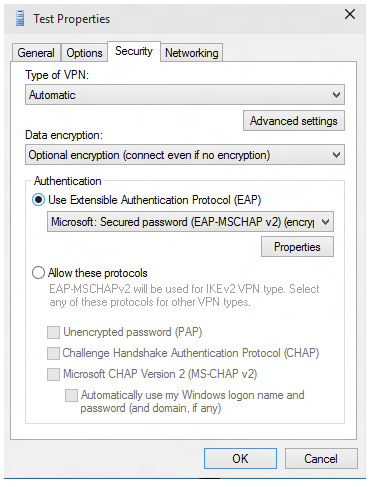
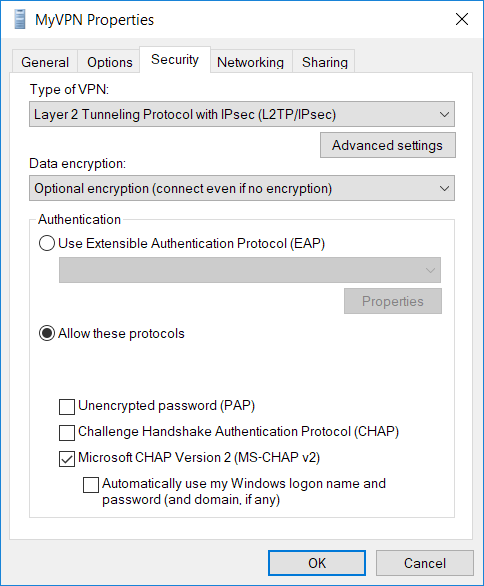
Step 3: Configure MS-CHAP on the Client | CompTIA Network+ Video Mentor: Configuring an L2TP-Based VPN | Pearson IT Certification

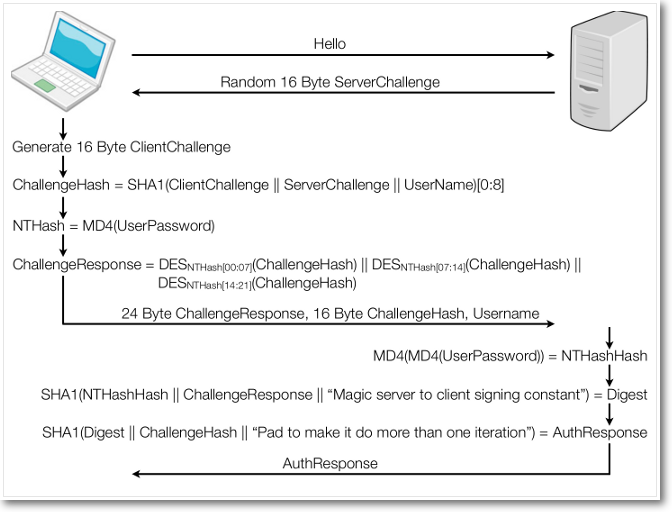
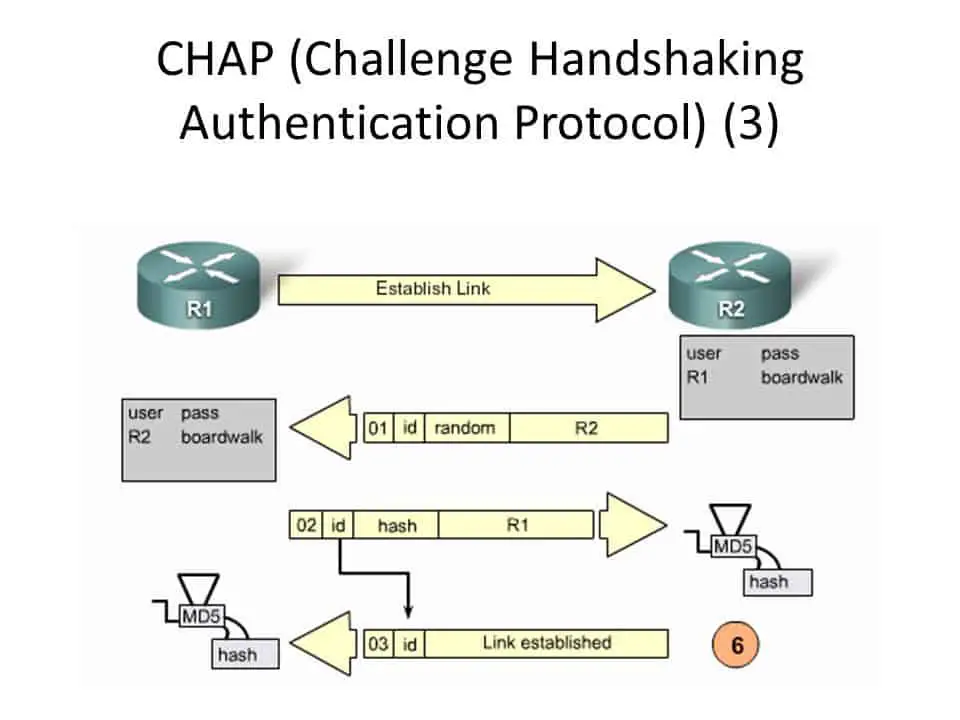
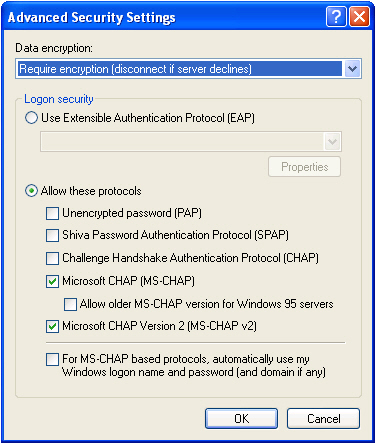
windows - Does a VPN utilizing PPTP and MS-CHAPv2 without encryption pose a risk to security? - Information Security Stack Exchange
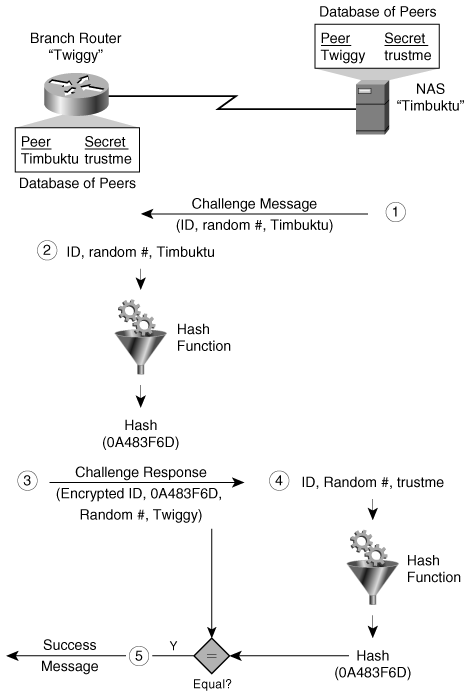
Authentication and Identity Protocols :: Chapter 2. Basic Security Mechanics and Mechanisms :: Wireless lan security :: Networking :: eTutorials.org